Jacob Roach / Digital Trends© Provided by Digital Trends
The completely redesigned Dell XPS 14 and 16 came out this year as two of the most divisive laptops in recent memory. No, it wasn’t just the capacitive touch buttons or invisible trackpad that caused an uproar — it also moved to soldered RAM. This was a big change from the past, where the XPS 15 and 17 were both celebrated for their upgradability.
Of course, Dell isn’t the first to make the transition. In fact, they’re one of the last, which is what makes the decision so much tougher to swallow. Where soldered RAM was previously limited to just MacBooks and ultrabooks, it’s now affecting most high-performance laptops for gaming as well. Even the fantastic ROG Zephyrus G14 moved to soldered memory this year.
So, why do these companies keep moving in this direction? Is there any validity to their claims about better performance or allowing for a thinner chassis? I spoke with many of the major laptop manufacturers to seek out some answers.
What is soldered RAM and why should you care about it?
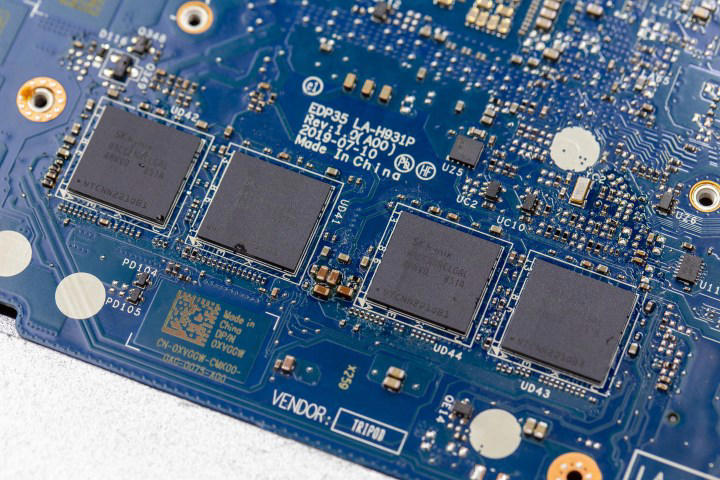
First, some background. The term “soldered RAM” refers to a type of computer memory that is permanently attached or soldered onto a laptop’s motherboard. Needless to say, that makes it impossible to upgrade, or even repair.
Laptops generally either come with all of the RAM soldered onto the motherboard or with traditional RAM sticks that slot into the board and can be removed or replaced. The latter is referred to as small outline dual in-line memory modules (SO-DIMMs). However, some laptops these days may feature a mix of the two, with some RAM permanently soldered and an empty slot that allows for upgradeability.
It’s not all bad. Whether we’re talking about thin and light productivity laptops, budget notebooks made for casual use, or high-end gaming beasts, they’re all trying to save space, prolong battery life, and optimize cooling. Using soldered RAM can be one of those space-saving techniques that enable manufacturers to create even thinner laptops, and all three of the companies I spoke to about this confirmed that.


Luke Larsen / Digital Trends© Provided by Digital Trends
While laptop manufacturers generally seem to like soldered RAM, not all end-users are onboard. The reason why enthusiasts across various forums and Reddit communities aren’t happy with the rise in soldered RAM is that it directly affects the value of the laptop that you’re buying. It makes the laptop’s memory impossible to upgrade in the future, and the repairs get trickier.
For some people, this isn’t a problem. Electronics, computers included, have never had shorter lifespans than they do now, and laptops are one of the things that get replaced every few years. Most users think of buying a new laptop before they ever think of wanting more RAM. After all, new graphics cards and processors come out every single year, enticing consumers to go ahead and replace their existing laptops with something newer and better. However, for power users, the lack of upgradeability is increasingly becoming a problem.
Why are laptop makers subjecting us to this? If you’d ask Reddit, they’d tell you it’s planned obsolescence, but is that all there is to it?
Despite spending over two months working on this article, I still feel like the topic of soldered RAM versus socketed options remains unexplored. Each type exists in its own niche, and now, there’s a lot of migration between one niche and the other where there wasn’t much before. We’re now seeing soldered RAM in gaming laptops, whereas previously we’d only see it in productivity machines.
Is this trend going to stick around? Most likely, although it’s hard to predict to what extent. One thing is clear, though — there are tangible benefits to companies using soldered RAM, and all the people I spoke to while writing this agree that they outweigh the downsides, but how that applies to the end-user is a bit more complicated.
What makes soldered RAM popular?

Greg Davill© Provided by Digital Trends
To find out what’s so great about soldered RAM, I spoke to Haval Othman, who is a senior director of experience engineering at HP. Othman made it clear that there are situations where he and his team would prefer to use soldered RAM, but it’s not a go-to solution for everything. “The main two reasons I could think about from all the strategic decision-making to using soldered RAM or socket RAM are the thermals, the efficiency, and the form factor,” Othman said.
Let’s break this down a little bit.
It saves space
If there’s one thing and one thing only that soldered RAM is indisputably good for, it’s saving space. Othman explained the benefits, saying: “If battery life, mobility, form factor (thin and light), and power efficiency are my priority among other design choices, then my mind immediately goes to soldered RAM; because that’s where soldered RAM can be beneficial and power-efficient, which will lead to longer battery life. Plus, it’s going to give me more space on the motherboard, so I can design the product thinner and lighter. […] If we want a thin product, the trade-off is soldering more of the devices onto the board.”
This tracks. In a laptop, there’s only so much space that can be used for components, and that free space grows smaller by the year to make ultrabooks possible. They’re an industrywide trend that was first popularized by Apple, and the rest of the laptop manufacturing world quickly caught on. Each year, laptops are released thinner and lighter, and that means having to squeeze the components together in new, innovative ways.
Apple’s way of getting around this was to start using its own system-on-a-chip (SoC) that integrates the CPU, the GPU, and the memory into a single chip. Other companies have to make do in different ways, and this is probably one of the biggest reasons behind soldered RAM.
Soldering the memory down onto the motherboard means that it can be attached almost anywhere within the laptop instead of being slotted into a specific part of it. It effectively makes the laptop thinner by cutting back on the space that the RAM module takes up. The space saved by soldering memory can be used for other things, such as a bigger battery.
It’s cheaper and easier to produce — or is it?
Not only are soldered modules much thinner, but rumor has it that they’re also easier to put together. With a RAM slot and a memory stick, you’d need an engineer to work on each laptop as it comes off the assembly line. Soldered parts don’t need that much human supervision and can be produced entirely by machines. Let’s not forget that they’re cheaper all on their own, without even considering the manpower required — they use fewer parts.
“It actually costs more to put a socket on the board than it does to solder RAM onto the board. On the other hand, of course, you can make one board and do different RAM configurations if it’s socketed. So it’s always a trade-off. As we plan these products, there are trade-offs every step of the way,” said Othman, confirming my suspicions.
It’s hard to say how much this affects the decision to use soldered RAM, though. All three companies that I spoke to stress the form factor much more than any tangible cost benefits. Tom Schnell, senior distinguished engineer of Dell Client Solutions Group, notes that this doesn’t make much of a difference. “There is no effect on manufacturing as the DRAM packages are standard. There is no impact on the retail price of our laptops,” Schnell said.
Stuart Gill, director of global media relations, campaigns, and corporate content for Lenovo, agreed with that: “Both soldered and socketed RAM designs are now quite mature. As a result, we see no impact on the manufacturing process and, therefore, the cost to the consumer.”
It seems that, although beneficial to the manufacturing process, the cost and the ease of production don’t play a big part in companies choosing soldered RAM.
It can be faster and more efficient


Luke Larsen / Digital Trends© Provided by Digital Trends
Modern laptops often use low-power DDR memory (LPDDR) as opposed to the DDR4 or DDR5 we see in desktops. These power-saving modules are a good deal for laptops, as they can help prolong battery life, but they’re always soldered. Another bonus stems from the thermal efficiency, as thoughtful placement of soldered RAM can make for a more streamlined mainboard design, optimizing the component layout. Lastly, some processors have higher frequency caps for LPDDR memory than they do for socketed RAM, with Meteor Lake maxing out at LPDDR5/X-7467 and just DDR5-5600.
As a result, it’s no wonder that many sources praise soldered memory for its performance. HP’s take on this is that bandwidth plays a part. “There’s also the issue of the bandwidth of the memory. On an SO-DIMM, it’s relatively limited bandwidth; while when you solder the memory chips onto the board, you can build it for a much wider bandwidth. And with things like the modern chips with the AI processors and things like that, that memory bandwidth is really important — so that’s part of the performance story and part of the requirement that makes soldered memory something that you almost need compared to socketed memory.”
This makes sense given that this type of memory is still more prevalent in productivity laptops, which are also more likely to benefit from things like the neural processing unit (NPU) found on the latest Intel Meteor Lake CPUs.
Dell’s Tom Schnell weighed in on the matter by saying, “Soldered RAM can achieve good performance because it does not require a connector or secondary PCB (printed circuit board), and because the total signal channel length can be shorter. However, the design is still limited by the best speed of the RAM and overall memory architecture.”
Schnell explained that this performance boost might not ever make any difference to consumers. “An increase in bus speed can have a 3-5% system performance improvement, but that improvement may not be noticeable at a customer level because system memory may not be the key limiter in system performance. For example, if the storage SSD is the system bottleneck, then a small improvement in memory performance won’t matter.” Schnell also noted that battery life isn’t as big a factor as some make it out to be: “There is minimal impact on power efficiency.”
It’s more durable, but …
This may not come as a surprise, but soldered RAM tends to be more durable than SO-DIMMs. Everything is fitted nicely and neatly, not to mention that it’s stuck to the motherboard for all of eternity. There are no moving parts, and the same cannot be said about RAM sticks that go into a particular slot.
Othman notes that HP has been happy with the stress tests it performed on its laptops. “In all our tests that I have seen for durabilities, they have a very high rate of success because of [the RAM being] fully integrated with the motherboard. But that’s not been the major strategic decision-making point for using soldered RAM versus socketed RAM.”
There’s a pretty high price to pay for this durability, though. If something does happen to soldered RAM, the repairability is … limited, to say the least.
The dark side of soldered RAM


Luke Larsen / Digital Trends© Provided by Digital Trends
With all of the perks of soldered RAM I just talked about above, you might be scratching your head and wondering why people are even complaining. Well, it’s not all as peachy as that, unfortunately, and those complaints are valid.
There are some glaring downsides to using soldered RAM. Laptop manufacturers can get away with them, because hey, for many users it just doesn’t matter. However, for those who care, the laptop market is slowly becoming a minefield where they have to dodge all the laptops that come with soldered components, including RAM and storage.
So, what’s so bad about soldered RAM?
For starters, the lack of upgradeability. This is not a problem for many laptop owners, but for those who notice an otherwise decent laptop start to run into memory issues, not being able to upgrade their laptop memory from 8GB to 16GB or 16GB to 32GB can be an obstacle. HP is aware that this can be a problem for some of its customers — namely, for gamers.
“Now, the other problem where you’re going to hear complaints is the upgradeability. Gamers in general want to be able to change and customize everything. But then, if you’re aiming for the thin and light, and the mobility, that’s where you need to go,” Othman said. He then noted HP’s Omen Transcend 14, the type of device that targets student gamers who value the thin-and-light form factor over upgradeability.
The next potential issue is the ability to repair the notebook. If the RAM module is soldered and it fails, there often isn’t much that can be done about it. As it’s permanently attached to the motherboard, the typical repair process involves replacing the entire motherboard — and that can cost a pretty penny.
Othman told me that HP hasn’t dealt with any cases of repairability problems caused specifically by soldered RAM. However, he also admitted: “If the issue is specifically [related to soldered RAM]; if someone has a burned RAM for example, in that case, the repairability will be much more difficult for the companies to do. It won’t be straightforward like with socketed RAM.”
If the laptop is still covered by warranty, swapping the entire motherboard isn’t going to be a problem. However, once that time’s up, you’re looking at some costly repairs.
Those are the two major problems, but they lead to smaller nuisances. For instance, having to decide about memory capacity at the time of purchase isn’t ideal for many. If you wanted to buy a laptop right now, you’d be faced with a choice. You’d either have to avoid models with soldered RAM entirely — which isn’t always easy, as this often isn’t listed on the spec sheet — or you’d have to spend extra to future-proof your device and get enough RAM right away.


Luke Larsen / Digital Trends© Provided by Digital Trends
This is one of those things that lends some legitimacy to the whole “planned obsolescence” theory. Laptop makers are allowed to charge extra on models with more RAM; an upgrade from 16GB to 32GB can often cost between $100 and $300, depending on the model. With upgradeable RAM slots, users can just buy a couple of SO-DIMM sticks for as low as $80 for 32GB. Having no option to upgrade means either switching to a different manufacturer or accepting the price of the model with more memory.
It’s not ideal, and it’s not consumer-friendly — but it’s the reality of the laptop market right now.
Is soldered RAM bad?


Digital Trends© Provided by Digital Trends
If you’re wondering whether soldered RAM is bad, and if you should avoid it the next time you buy a laptop, I’ll let you in on a secret: There’s no universal answer to that question.
Soldered RAM is pretty bad if you care about upgradeability. If you want to buy a laptop that will last you years, and you want to have the option to improve it as time passes, models that come with their memory perma-attached just aren’t for you. If you don’t mind it, however, there’s little to no reason to avoid it, but be prepared that if something does go wrong, costly repairs will be on the horizon.
This might be why the outcry on websites like Reddit has been so loud lately. After all, some of the previously top-shelf gaming laptops have now made the stealthy switch to soldered RAM, and many users aren’t happy.
As I mentioned at the beginning, the 2024 Dell XPS lineup comes to mind. Everything is soldered in Dell’s new laptops, meaning that you can say bye-bye to upgradeability and repairs. Even the excellent Asus ROG Zephyrus G14 comes with soldered memory, which puts it at a disadvantage when compared to laptops like the Razer Blade 14.
For now, I think that the main problem that I personally have with soldered RAM is that outside of pushing for thinner and lighter laptops, there’s little to no benefit to customers. Despite trying to find out why exactly this type of memory is becoming more prevalent in laptops that may not be becoming thinner, I’m still unsure. I get that it’s the only way to make laptops thinner — but if the notebook is still the same size from one generation to the next, only the RAM is now soldered, what did we gain? If the performance benefits aren’t massive, was it ever worth it for the end-user? Doesn’t feel like it.
The good news is that SO-DIMM memory might eventually be replaced by the CAMM2 standard. Recently approved by JEDEC, CAMM2 is said to be significantly thinner, and it’ll be available both in soldered and non-soldered variants. Using CAMM2 will allow laptops to stack up to 128GB of RAM, and the frequencies are said to be going up, too. CAMM2 can also activate dual-channel memory with just a single module.
When I spoke to Dell, Tom Schnell shared my hopes for CAMM2 being a good solution to this dilemma: “This is a big reason why Dell brought CAMM to the JEDEC standards body in 2023 — to solve for performance memory ceiling limits with SO-DIMM while also being a modular design. ”
It’s too early to tell, but it does sound like CAMM2 memory might solve just about every issue with SO-DIMM, allowing for thinner laptops and — hopefully — a return to upgradeability. But until then, all you can do is wait and look into some of the few upgradeable laptops still left if this is an important factor to you.